By: Malak Al-Saqri
In the age of Internet and revolutions, it has become hard to keep your personal life safe and private. These days it's very easy to reach a person's contact, full name or where s/he lives, you can get to know a person and his/her entire family without meeting them in reality! it's hard to admit this ugly truth, but strangers can actually enter your own house without taking permission!
Not by doors or windows but through this small digital screen, they can share your own life with you! So, it is the perfect time to address this question, Is our personal information safe in this digital world?
What is the definition of private information?
First, let's get familiar with the origins of the word ‘Privacy’, it is derived from the Latin word ‘Privatus’ which means the state of being in retirement from the company or the knowledge and observation of others.
We can define private information as any data that may specify a person's identity or holds deep delicate pieces of information a person wants to keep hidden from the public. But people tend to share and digitize almost every aspect of their lives, from managing their finances to communicating with friends and buying goods. For example, medical information, Tax information, and credit card information, all can be considered sensitive information so people expect to have their personal data protected and their behavior not tracked when connected to the internet.
Why is our information in danger online?
You may have heard a well-known saying about the digital world “If you’re not paying for a product, then you are a product’’. Businesses consider consumers` data as a part of their marketing strategy. It's time to realize that our personal data is worth money. This data brings a clear vision into how consumers navigate and experience particular products or services which helps them customize their products to meet clients' needs and strike the right pain points, desires, and political perspectives of an audience, such as social media platforms.
Criminals can use our data for blackmail by stealing sensitive information or threatening to reveal things we want to stay hidden. They may steal the identity of a person's, medical records or break into accounts with payment details.
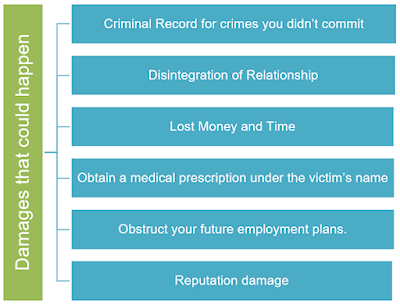
The consequence of identity theft
According to the FEDERAL TRADE COMMISSION (FTC), every 14 seconds there is an identity theft crime. Redressing the situation will also rely on how quickly you responded and how much damage was caused.
What kinds of risks threaten our online information?
People often fear about their personal data being observed or hacked while using the internet. So, it’s very important to know what threats you could face to deal with them professionally.
Poorly secured system (vulnerabilities)
Some systems are developed without security in mind and weaknesses in hardware, software or any of the system procedures. Poorly secured systems have a gap that hackers can use to easily breach the system.
Social Media attacks
An attacker can use social media to spread Malware to damage or gain access to computers through social media messages as most people intend to randomly share information about themselves on social media accounts.
Phishing
It is one of the hacker techniques that are on the rise to attack users' sensitive or financial information by using hyperlinks, attachments, or messages with unusual senders to reveal personal information such as passwords and credit card numbers which can be one of the most devastating effects of hackers' attack. It is worth noting that Using SSL/TLS encryption to protect sensitive data and prevent data loss can highly protect your website server from unauthorized access, which is one of the privileges that ESKADENIA Software provides.
Insider threats
Insider threats refer to those who are coming within the organization such as the organization's employees. They can use their legal access to the company data to breach sensitive information or damage the system. These kinds of threats can be endangering the confidentiality, integrity and availability of sensitive information and systems.
Information security
It is a high priority to have a safe internet atmosphere that can be trusted when sharing personal information online without being compromised, revealed, or badly amended. The right way to prevent these consequences is to have security rules that guarantee the protection of users' personal data through the Internet. Information security is the act of protecting data against unauthorized access through a set of procedures and standards without being tracked when connecting to the internet.
Here are some tips to maintain your information secure:
- Create a Strong Password
I know that using simple, short passwords is easy to remember but this can cause a serious threat to your online security. Keep away from the most commonly used passwords and remember that random passwords are the strongest!
- Don’t leave your device unwatched
If you store personal or work information on your device, make sure you don't leave it unattended, even if you're temporarily away from your computer. Lock your screen to prevent others from accessing it. And keep in mind never hesitate to instantly report lost devices or data to your manager or concerned authorities.
- Ensure a secure Wi-Fi connection
Wi-Fi connection is the gate to connect your computer with the outside world. Unprotected networks risk exposing your online activities and can be used for illegal purposes, leading to potential consequences for you. Encrypt your network, update router settings, software, and username for enhanced security.
- Don't hold data for any longer than necessary.
As we discussed before, if our delicate information falls into the wrong hands, it can lead to different types of threats. If you collect and use personal data fairly and lawfully, you cannot keep it longer than needed. Remember that when you no longer require personal data, you must ensure that it is erased or anonymized. This will undoubtedly lessen the risk.
So, to wrap it up, it's crucial to be aware that technology is a double-edged sword. Be wise to avoid the risks and take steps to protect your information. By using strong passwords, being cautious with what you share, and staying updated on security measures, it is never too late to safeguard our digital lives. Remember, it's better to be safe than sorry in this digital age! Stay informed, stay vigilant, and keep your data secure.


No comments:
Post a Comment